Make This Password Policy Your Own
The following info is provided to help you create a Password Policy. Use the template as a guide, and make it work for your company.
Texas Technician provides your company with a "Password Manager". This program can be locked down, to the point where it can only be opened on a specific computer, if you see that being necessary.
Something to keep in mind.
The more "SECURE" you make something, the less secure it becomes. Adding too many "road-blocks" will make your staff less likely to follow protocol.

Example of an ineffective password policy:
Years ago I had a call at a large company. I needed the password to the client's PC. I asked the nice lady (the client) for their password.
They lifted up the keyboard, and a dozen sticky notes fell down.
She riffled through them and said: "I think it's this one!"
I asked why she had the password to her computer written on a sticky note, under the keyboard. I also noticed that each sticky note was some iteration of: Her-Dogs-Name-1a, Her-Dogs-Name-2a, Her-Dogs-Name-3a, ...
She stated: "Our IT department makes us change our password every 30 days. I can't remember it, so I have to write it down. Everyone else does it too. Just don't tell the IT guys..."
The IT department created an arbitrary and unnecessary road-block. In the hopes of being "SECURE". And unwittingly made their environment very insecure. With this small bit of info, and my trusty laptop. I could have guessed, by hand, every user's password.
Password Complexity:
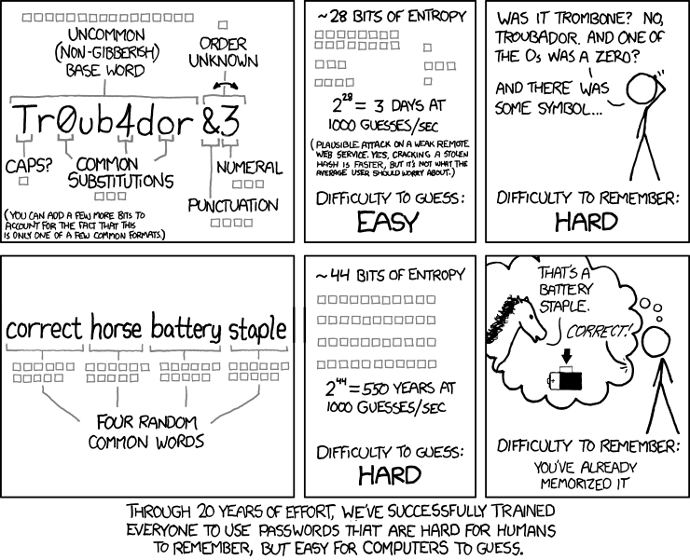
Don't make passwords hard, make them long.
The incorrect conventional wisdom was that passwords needed to have lots of symbols and mixes of alphanumeric characters : "P@$$w0rD1"
Turn's out that advice is bogus. Passwords like this are easy to "brute force" and are hard for you to use.
Don't take my word for it.
Bill Burr, former manager of "National Institute of Standards and Technology". Is the person responsible for popularizing this outdated password policy. He said: "Much of what I did, I now regret".
Make your passwords long, add a few symbols and some numbers. The best way to create a new password is to use your password manager's "Password Generator":
Password generator used in KeyPassXC:
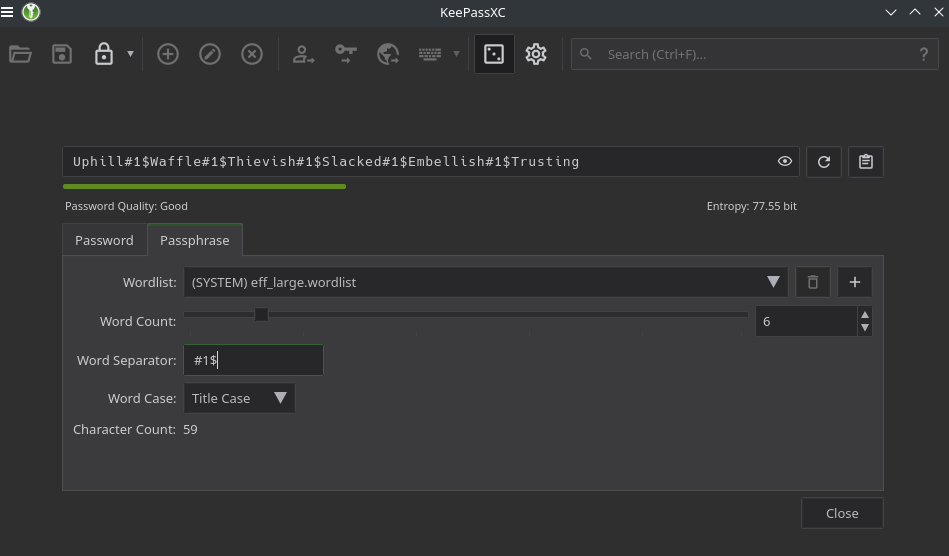
This is something known as a "Passphrase". Its a list of random words picked from a very big dictionary. Separated by symbols and numbers.
Passphrases are easy to digest and type. But are hard to "brute force". Provided that the Passphrase is at least 50 characters long.
Some companies just don't get it. They set arbitrary limits on password length and strength. e.g. "max length is 30 characters".
In the case that you cannot use a long Passphrase, use a truly random password:
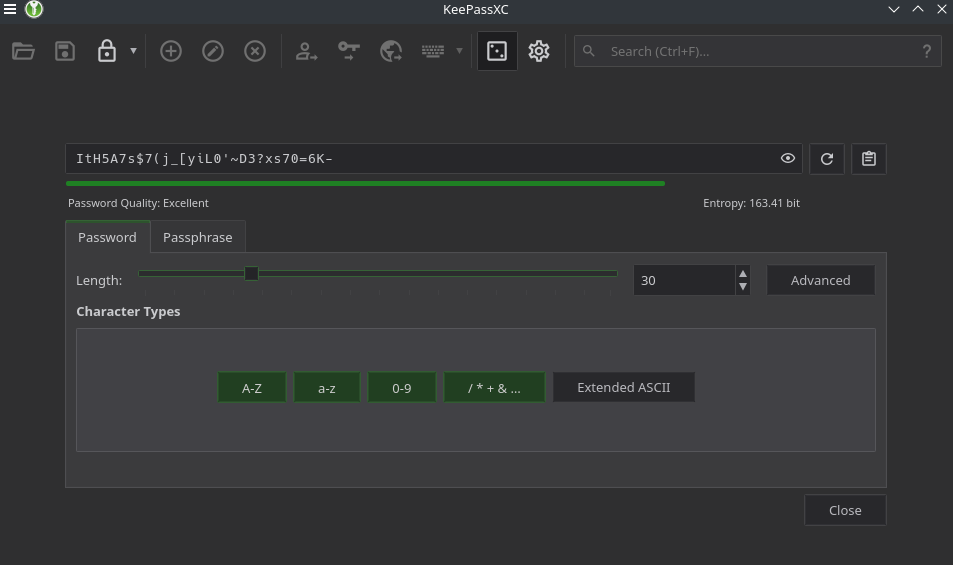
These are not easy to type, share, or read out-loud. But they are very hard for a computer to "brute-force".
What's a "Password Manager"?
It's a program that manages your passwords :)
More specifically, it's a purpose-built program. Designed to be as secure as possible.
Password managers centralize your company's passwords in one secure database. Depending on the password manager you chose, you can setup "Hierarchical or Granular Rights". Meaning you can grant certain users access to only a few passwords.
Example: HR only needs access to the passwords used in HR, but not the IT Department's passwords.
Password Manager Features:
- Centralize storage of passwords in an encrypted database.
- Generate passwords at the click of a button.
- Control who gets access to what passwords.
- Alert you when a password is about to expire.
- MFA, SSO integrations.
- Clipboard security: When you copy a password from a manager. Your computer's OS knows it is from a password manager. And the entry in the clipboard is auto-deleted after a certain time. (for KeePassXC the default time limit is 10 seconds).
At Texas Technician, we include a password manager in all Managed IT Service Plans.
There is a crazy amount of password managers. Some of the best are FOSS (Free and Open Source Software).
|
Name: |
Price Model: |
Notes: |
|
FOSS |
|
|
|
FOSS, and "Freemium" (pay for advanced features) |
|
Storing passwords on external servers is not advisable; we
utilize self-hosted password managers for enhanced security.
Key Advantages:
- In case of a network failure, your local database remains accessible, ensuring uninterrupted access to your credentials.
-
Regular backups of your database are made to your company's proprietary backup solution, offering an additional layer of security.
-
Your encrypted password database, stored on your encrypted hardware and shielded by your own firewall, is less likely to be targeted than a company like LastPass (a password manager company).
Being small does not mean you are not a target. You are, everyone is, a target to hackers. But your password manager is more likely to be breached by an employee sharing their Password Manager's login credentials, than it is to be breached by an army of dedicated hackers.
Excel is NOT a Password Manager!
Password Protected Spreadsheets Are NOT Secure
I once had a bank manager show me his "password manager". A password protected Excel spreadsheet.
Excel uses 256-bit encryption (very good).
The problem is that ALL of the passwords get decrypted when you open the document. And there is no "clipboard security".
There's a type of malware which steals data by running in the background and just reading your RAM (which is where the data is stored when you open a document).
Whereas in a "Password Manager" only one password at a time is decrypted.
And any password copied to your clipboard is auto-deleted after a few seconds.

What's MFA/2FA ?

Always use 2-Factor Authentication
MFA (Multi-Factor Authentication) and 2FA (Two-Factor Authentication) are terms used interchangeable in the industry.
It's an extra layer of protection used to login to a service. After you put in your password, you also have to enter your MFA/2FA code.
The most common MFA/2FA are:
- TOTP (Time-based One-time password): a "key" is shared with your password manager (or authentication app) and the service your logging into. This "key" generates a 6-digit number every 30 seconds. When you login, a second prompt appears asking you for the 6-digit number.
- OTP via email or text: a code is sent to your email or phone.
TOTP is better than OTP. TOTP keys can be shared with any "Authenticator App".
I have my "Authenticator App" synced between two phones. One is stored at my office. The other is always in my pocket. In the event I lose my main phone. The backup still has all of the TOTP keys safely stored.
Always use MFA/2FA when possible. Yes, it's annoying to spend 10 extra seconds logging into something. I assure you, it's much more time-consuming and annoying to recover a hacked account.
How Passwords Get Hacked!
There's an endless way to hack passwords. For brevity's sake, I'm going to list just a few. If your interested in the crazy amount of ways you can be hacked. Watch this:
Common Methods to Hack a Password:
- Brute-Force: A program tries to guess your password over-and-over again. Until it breaks in. This method works, but takes forever and needs decent computational power to be effective. Unless the password is not secure (short).
- Dictionary Attack: A program uses a list of common words to guess your password. A hacker can input certain words to be used first, e.g. your pet's names. The program uses these words combined with symbols and numbers to guess your password.
-
- This is why you should never use personally identifying info in your passwords. It's shocking how fast a dictionary attack can happen when the keywords in your password are : "Patches", "Muffin", "MyNickName"...
- Social-Engineering: Someone pretends to be someone with authority to get your staff to disclose a password. This is the most effective way to date, to steal a password. Because the biggest security risk at every location, sits between a keyboard and a chair.
How to Mitigate Social-Engineering:
- Hierarchical or Granular Access: Don't give someone access to passwords they don't need. You cannot disclose what you don't know.
- Only Allow Secure Sharing: Don't disclose passwords over the phone, through text, or plain email.
Share passwords by: -
- Sending a password protected Word document via email,
- Use your cloud service's secure sharing (the recipient is emailed a link to a document that can only be downloaded once, and can only be downloaded by the email recipient).
- Institute a "Verification Protocol": This is really simple. If someone calls to get a password or other sensitive info. Verify who they are first.
Example Verification Process:
Someone calls claiming to be from "Texas Technician" and asks for a password:
- Inform them that you have to verify who they are before you can give that info.
- Ask for some form of personal identifying info:
-
- First and Last name. (some companies refuse to allow employees to give their last name).
- Employee ID.
- Direct Callback Number (help desks will sometimes have direct callback numbers, or extensions).
- Ask for Texas Technician's company phone number.
- Inform the person you will have to call them back to verify who they are.
- Google the phone number to Texas Technician.
-
- If this number is different than the one the caller gave you. Notify your manager of a possible hack attempt.
- If it matches the number given to you. Call the main line and ask to speak to the caller.
-
- If that person doesn't exist. Notify your manager of a possible hack attempt.
This is not a fool-proof method. The best option is to refuse sharing passwords with outside sources, period. Texas Technician will rarely, if ever, ask you to disclose a password. We do ask customer's to enter their passwords, if needed. Texas Technician does not store any of your passwords, except the admin passwords required to do our work.